Documenting the full process of cracking a Follow invite code, learning about LSB steganography and the use of the StegOnline tool.
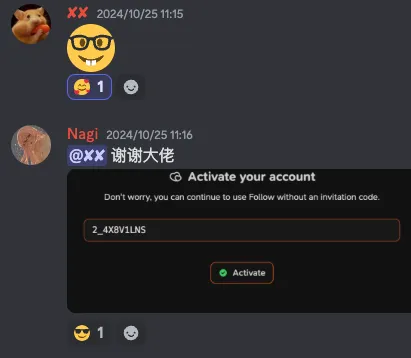
The Journey of Cracking the Follow Invite Code
While browsing Follow’s Discord during a boring class, I was trying to snag an invite code. My hands were too slow, though; the ones given away directly or with just one digit masked were usually gone by the time I saw them. Then, I came across the following puzzle:
Scanning the QR code yielded the message: “The invite code is hidden ‘inside’ the image.” OK, challenge accepted 🤓.
Knowing it was unlikely to be simply embedded visually, I still stared at it for a minute and even asked GPT-4o to analyze it multimodally. Unsurprisingly, that led nowhere.
It was highly probable that it was steganographically hidden, much like a watermark (guessing here since I’m not an expert). AI suggested it might be LSB (Least Significant Bit) steganography. The basic principle is as follows: 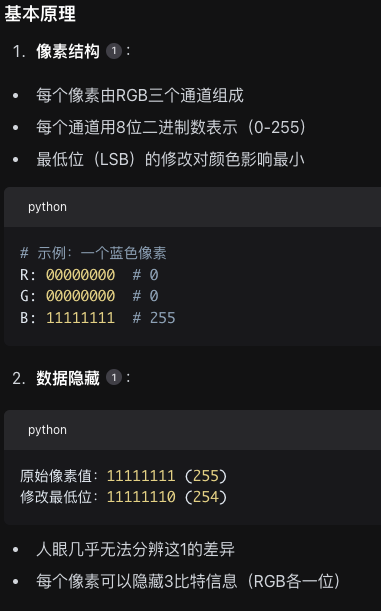
It recommended the Stegsolve tool. I have to praise devv.ai’s 3.5 Sonnet + web search—it’s incredibly powerful. I then searched for an online version I could use immediately, and the star of today’s show appeared: https://georgeom.net/StegOnline
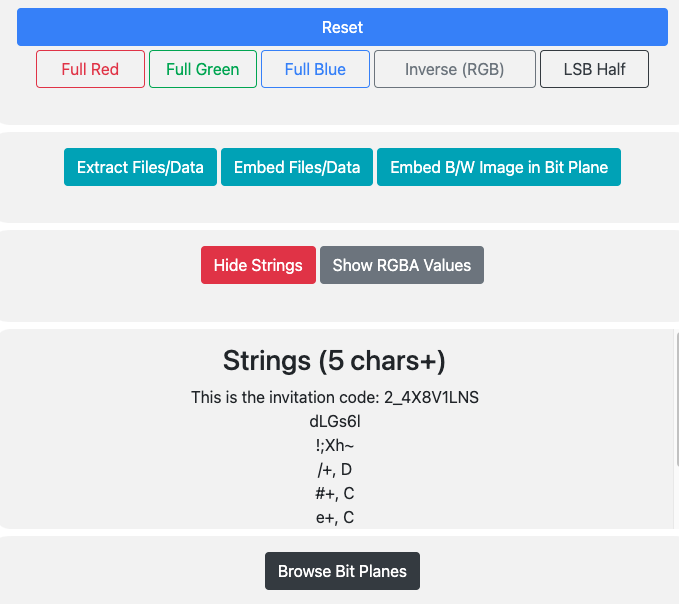
The result was an instant win… the cracking process wasn’t as rough as I imagined. Thanks to the creator for taking it easy on us!